Information security
The risks of information leaks caused by internal fraud targeting information retained by companies and by disruptions to business activities caused by cyber attacks have been increasing in recent years.
In order to provide reassurance to our stakeholders, we are placing importance on the protection of our proprietary information, which includes technical information, management information, and other confidential information that are the sources of Murata’s competitive advantage as well as personal information in our possession and information provided by clients, customers, and partners. In doing so, we designate information security as a material issue and continue to promote initiatives toward this end.
We aim to minimize risks by running through the information security risk management PDCA cycle every day, in order to prevent potentially serious incidents from happening, under the management of officers responsible for information security (executive officers and the Corporate Division ESG/HR Management Department Manager).
In FY 2007, Murata established an information security subcommittee as a lower branch of the Risk Management Committee, which incorporates recent risk trends and related guidelines from Japan and overseas based on international standards (ISO27001) to implement information security management. Specifically, Information Security Basic Policy, Information Security Management Regulations, Privacy Policy and other rules are enacted to develop and operate information security measures in terms of human, technical, and physical aspects. The information security subcommittee periodically meets to examine new and persistent risks, and to propose and implement measures.
Topics discussed by the Information Security Subcommittee are supervised by the Board of Directors through the Risk Management Committee.
In addition to implementing information security management initiatives based on the international standards mentioned above (ISO27001), our major domestic and overseas sites (including our headquarters) have been certified under Trusted information Security Assessment Exchange (TISAX), an information security evaluation conducted by the German Association of the Automotive Industry.
Going forward, we will continue to get more of our sites certified in addition to conducting our usual internal and external audits and examinations, in order to spread awareness and enhance information security management.
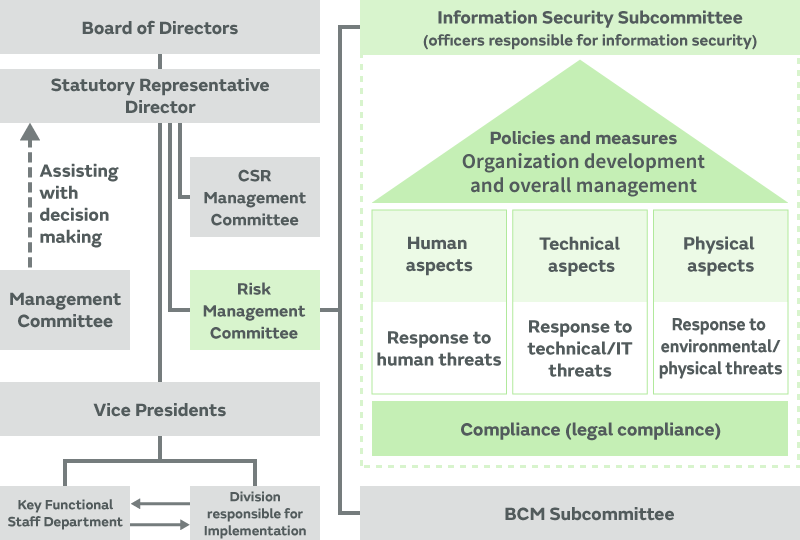 Information security subcommittee system diagram
Information security subcommittee system diagram
Human aspects
Information security related rules are described in employee handbook and the pledge with employees. In addition, the Information Security Guidebook, which explains the rules in an easy-to-understand manner, is written and distributed in Japanese, English, and Chinese so that all officers and employees in Japan and overseas can understand information security and handle information in the proper way.
Murata also implements annual training for all employees to increase their awareness of information security, phishing email drills, in-house training by employee level (new employees, etc.), and information security training for telecommuting employees.
(Fiscal 2022 Global training ratio* = 96% [*Training ratio = (Number of sites that have conducted training) / (Total number of sites)])
Technological aspects
In order to deter leaks of Murata’s confidential information and personal information as well as interruptions of business activities due to cyber attacks, we continue to strengthen anti-malware measures, hardware asset management, firewall construction, Internet communication checks, ID management, system access controls, and diagnosis and countermeasures for vulnerabilities in current information systems.
Moreover, we are globally collecting and monitoring various logs to construct a system for responding to incidents which may become a security accident. In particular, we continue to strengthen security at the plant sites that form the basis of our business activities, and promote responses and countermeasures to constantly changing cyber attacks and risks to maintain a stable and safe production system.
Physical aspects
To prevent unauthorized intrusions into premises at offices, sites and affiliated companies in Japan and overseas, access control of people and vehicles is carried out at all times. Security zones are established within business sites according to the level of security control, and various measures including access controls using ID cards, etc. are implemented in highly secure zones to prevent unauthorized internal and external intrusions. Moreover, in order to continuously improve the physical security level, we periodically diagnose and audit the operating conditions from the perspectives of early detection and evidence accumulation measures in addition to restricting people's movements and preventive measures, and we are promoting the construction of a system to horizontally deploy responses to accidents and incidents which may become accidents with other offices, sites and affiliated companies.